Cloud computing has become an essential part of many organizations’ IT strategies. While the cloud offers numerous benefits, including scalability, flexibility, and cost-effectiveness, it also introduces new challenges for protecting sensitive data.
As you migrate your data to the cloud, it’s crucial to understand the potential risks and implement robust security measures to safeguard your valuable information. One powerful technique for achieving this is data masking.
Understanding the Necessity of Data Masking in Cloud Environments

The adoption of cloud computing has grown exponentially in recent years, with more and more businesses moving their data and applications to the cloud. However, this rapid growth has also led to an increase in data breaches and cyber threats targeting cloud environments.
Recent studies indicate that data breaches are the top concern for organizations using cloud services. Moreover, data protection regulations have become stricter. For example, the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and the Health Insurance Portability and Accountability Act (HIPAA) impose strict requirements on handling personal data. Failure to comply with these regulations can result in hefty fines and reputational damage.
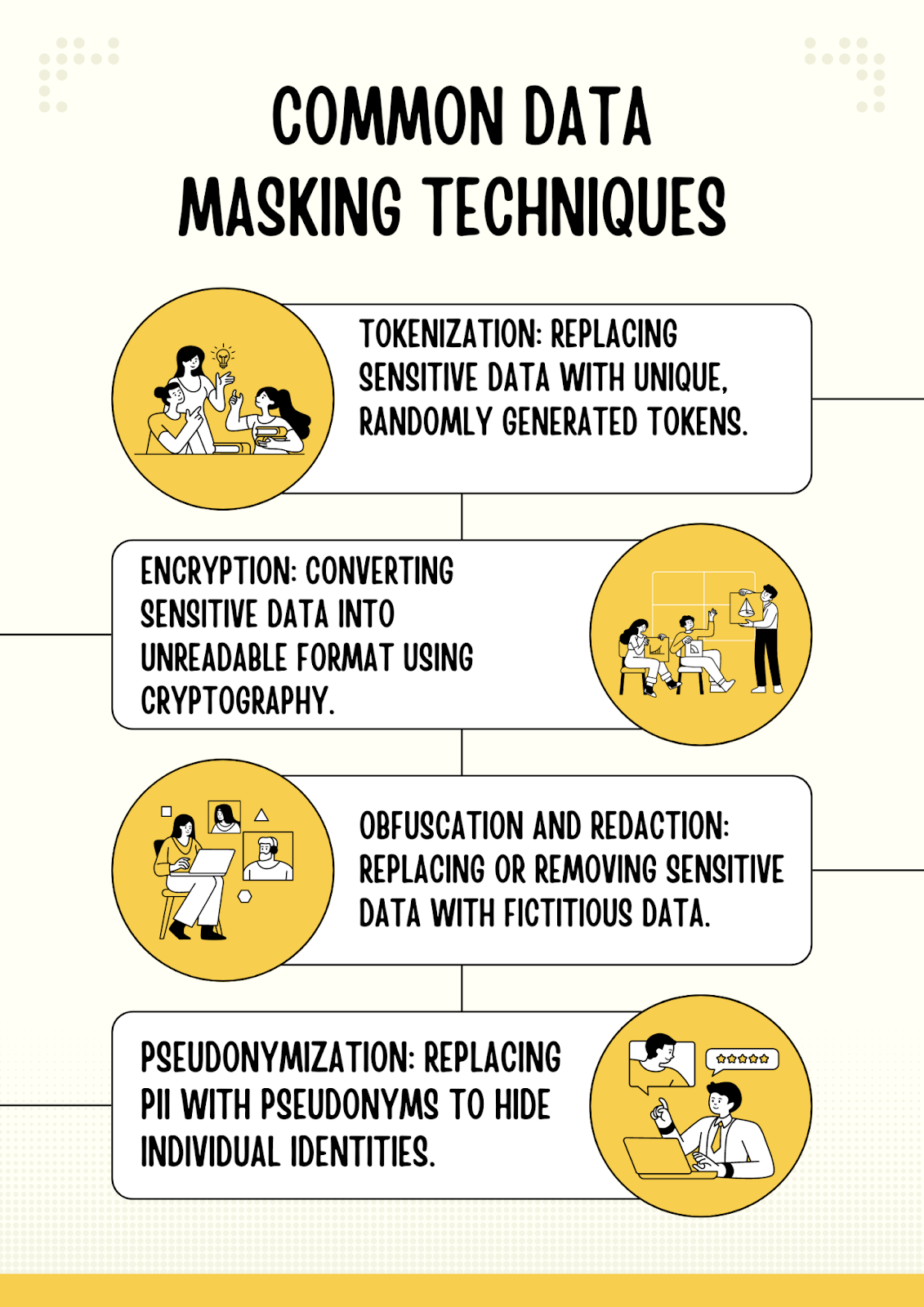
Core Principles and Techniques of Data Masking
Data masking involves obfuscating sensitive data while maintaining its format and structure. This technique is essential for protecting sensitive information from unauthorized access and ensuring compliance with data protection regulations. By masking sensitive data, organizations can safely use and share their data without compromising its confidentiality.
There are two main types of data masking: dynamic and static. Dynamic data masking is a technique that masks sensitive data in real-time as it is being accessed by applications or users. This approach is particularly useful for protecting data in production environments without impacting the functionality of the applications. With dynamic data masking, sensitive data remains hidden from unauthorized users, while authorized users can still access the data they need to perform their tasks.
On the other hand, static data masking involves creating a masked copy of the original data, which can then be used for testing, development, or analytics purposes. This approach is often employed when sharing data with third parties or using data outside the production environmen.
Implementing Data Masking in Cloud Computing
Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) are leading cloud providers. They offer various data masking solutions. You can integrate them into your cloud infrastructure.
These solutions often provide APIs and pre-built connectors that allow you to seamlessly integrate data masking into your existing applications and workflows. When implementing data masking in your cloud environment, it’s essential to follow best practices to ensure minimal impact on performance and usability.
This includes:
- Identifying and classifying sensitive data across your cloud infrastructure.
- Selecting the appropriate data masking techniques based on your specific requirements and the nature of the data.
- Testing the masked data to ensure it maintains its utility and does not break any dependent applications.
- Regularly monitoring and auditing your data masking processes to ensure they remain effective and up-to-date.
Advantages of Data Masking for Cloud Security

By implementing data masking in your cloud environment, you can:
Enhance Data Privacy and Security: Data masking helps protect your sensitive data from both internal and external threats, reducing the risk of data breaches and unauthorized access.
Facilitate Compliance: With data masking, you can more easily meet the requirements of data protection regulations, simplify audits, and provide assurance to stakeholders that sensitive data is being properly secured.
Enable Safe Data Sharing: Data masking allows you to share data with third parties, such as partners or service providers, without exposing sensitive information.
Support Development and Testing: By creating masked copies of production data, you can safely use realistic data for development, testing, and analytics purposes without risking the exposure of sensitive information.
Challenges and Solutions in Data Masking
While data masking offers significant benefits, it also presents some challenges, particularly when dealing with large datasets and ensuring the utility of masked data. Some common challenges include:
- Maintaining performance and scalability when masking large volumes of data.
- Ensuring that masked data retains its format, structure, and statistical properties to maintain its usefulness for testing and analytics.
- Keeping up with the evolving threat landscape and new data protection regulations.
To address these challenges, organizations are turning to emerging technologies such as artificial intelligence (AI) and machine learning (ML) to optimize their data masking processes. AI and ML can help automate the discovery and classification of sensitive data, select the most appropriate masking techniques, and continuously monitor and adapt data masking policies based on changing requirements.
Choosing the Right Data Masking Solution for Your Organization
When selecting a data masking solution for your cloud environment, it’s important to consider several factors to ensure that it meets your specific needs and requirements. Some key considerations include:
Compatibility with Your Cloud Provider: Ensure that the data masking solution you choose is compatible with your cloud provider and can be easily integrated into your existing infrastructure.
Supported Data Types and Formats: Verify that the solution can handle the types and formats of data you need to mask, such as structured, semi-structured, and unstructured data.
Performance and Scalability: Evaluate the solution’s ability to handle large volumes of data and its impact on system performance, especially in real-time masking scenarios.
Ease of Use and Management: Consider the user-friendliness of the solution, including its interface, configuration options, and monitoring capabilities.
Security and Compliance: Assess the solution’s security features, such as encryption, access controls, and audit logging, to ensure it meets your organization’s security and compliance requirements.
By carefully evaluating your options and selecting a data masking solution that aligns with your needs, you can effectively protect your sensitive data in the cloud while minimizing any potential disruptions to your business operations.
Wrap Up
Data masking is a critical tool for protecting sensitive information in cloud computing environments. By understanding the core principles and techniques of data masking, implementing best practices, and staying up-to-date with emerging technologies and trends, you can significantly enhance the security and privacy of your data in the cloud.
As you navigate the complexities of cloud security, it’s essential to prioritize data masking as part of your overall data protection strategy. By doing so, you can not only safeguard your valuable information but also maintain the trust of your customers, partners, and stakeholders.
FAQs
1. How does data masking improve security in cloud computing?
Data masking hides sensitive information, reducing the risk of data breaches while maintaining data usability for cloud-based applications.
2. What are the main benefits of using dynamic data masking in cloud environments?
Dynamic data masking protects sensitive data in real-time without affecting application performance or user access.
3. Why is static data masking essential for cloud data sharing?
Static data masking ensures that shared data is anonymized, protecting sensitive information during testing, development, or third-party collaborations.



